
Why you must be ultra-conscious about your VPS (Virtual Private Server) security? How do hackers target your VPS and damage your trading system? How to Protect your VPS from Dos, DDos, and Malware attack? In this article, we’re going to be talking about the main threats to your trading infrastructure and the main precautions that you need to take to protect it.
In particular, we are going to be talking about cloud servers in this article, and I’m going to provide you with an overview of the fundamental measures to protect your infrastructure.
These standards and tips are all the product of our experience with systematic trading.
Contents
Threats to Your VPS
To protect your VPS from DDoS attack you should subscribe to only that Cloud Server Provider that offers DDoS Security feature and you should also deploy an Internet Security Suite or Antivirus. The combination of antivirus and firewall might also be a solution but not very much effective.
There are mainly three kinds of threats that can damage your trading system.
The threat of Malware and Viruses
The major threats are viruses and malware, which are potentially dangerous files that you can come into contact with when you use your computer.
Later on in this article, we’ll discuss that in addition to using a good antivirus suite, there are other measures you can adopt to protect yourself from this kind of threat.
For example, you should strictly avoid downloading untrusted potentially harmful files or using your VPS or cloud server for any use other than your business.
This is the best method to limit the risk of downloading malicious files that may slow down your machine.
Dos and DDoS Attacks
Another type of threat that we’ve identified is external attacks such as DoS attacks.
Where DoS which stands for “Denial of Service” and DDoS stands for (“Distributed Denial of Service”), which are very similar to DoS attacks but basically they are “distributed.”
Brute Force Attack and Generic Vulnerabilities
The third kind is the “Brute Force” attack, which we will see in more detail later in this article.
Finally, I’d like to give you an overview of some generic vulnerabilities that may threaten your machine, such as choosing an easy password or not changing some default settings in Windows.
It may be dangerous because, since these parameters are predefined, undoubtedly, they are easy targets for hackers. But let’s discuss the first category.
How to Protect Your VPS from Viruses and Malware?
When it comes to viruses and malware, the first thing to do is identify the risks and the main risk is that hackers steal your sensitive data.
For example, the confidential data that you saved on your computer, such as your bank account information or trading account credentials, passwords, etc.
If you get some specific virus or malware, the information may be stolen and even sent to third parties. Another high-level risk is that hackers may edit, delete, or encrypt your data files or even format your drives.
So, it’s important to be very careful about these types of threats.
Let’s move on to external attacks.
How to Protect your VPS from External Attacks
Some hidden viruses also exist which will never affect your files and sensitive data but will open your system port to provide access to hackers.
These viruses are more dangerous because they provide control of your system to hackers.
Fortunately, there are several effective solutions to protect your VPS.
The best way in my knowledge is using a good Internet Security Suite. Antivirus software can provide you security, but Internet Security suites are more promising as they also include antispam, firewall, anti-phishing, and anti-malware features.
These suites are certainly a more promising solution. However, the combination of firewall and antivirus is also good.
How to Protect Your VPS from Infected Files?
As I’ve already mentioned earlier, another essential measure consists in installing and using only software that is strictly important for trading.
This can provide great support because, in this way, you can significantly reduce the possibility of coming into contact with infected files.
For example, it’s recommended to download only the latest version of your trading platform, the latest plug-in of your broker, and other recent updates from the Microsoft website.
You should strictly avoid using the same computer for online entertainment or download emails, etc., because in doing so, there is a huge chance of stumbling upon potentially dangerous or infected files.
And then, it is also suggested, to avoid downloading or using any pirated or illegitimate software on your computer.
At last, it is recommended not to use cloud hosting clients like Dropbox, OneDrive, etc. because the transfer of malicious files to a Remote server may take place once it reaches Dropbox or OneDrive.
Consequently, it would copy the virus or the infected file onto the remote server as for the first point we talked about.
So, we can confidently say that any of these solutions may serve the purpose if they are used correctly.
How to Protect Your VPS from DoS and DDoS Attack?
As for DoS and DDoS attacks, where DoS stands for “Denial of Service” and DDoS for “Distributed Denial of Service,”.
They initiate attacks that aim to disable or make unreachable a system that provides a service to different clients, such as a remote server or a data server.
The mechanism of these attacks is bombarding the target server with access requests until this server loses its calculation capability or bandwidth to process all the requests and becomes unreachable.
The major difference between DoS and DDoS attacks is that in the case of DDoS attacks, the attack doesn’t happen from a single source but occurs in a distributed manner from multiple sources.
This means that the attack was initiated by several “attackers” that work simultaneously. This organized group of attackers is called a “botnet.”
How the botnet is formed is also very unique because usually, those who launch this kind of attack first try to infect the systems that will be part of the botnet, and these infected computers are known as “zombies”, and then these zombies will attack the targetted victim’s computer.
Protection Technique
The main risk, in this case, is server unreachability or unavailability, and the most simple protection technique, at least in my opinion, is to subscribe to a cloud server provider that includes DDoS protection.
That’s why it is our responsibility to investigate what kind of protection a particular cloud service provider offers against this type of attack.
The picture below shows how this type of attack works.
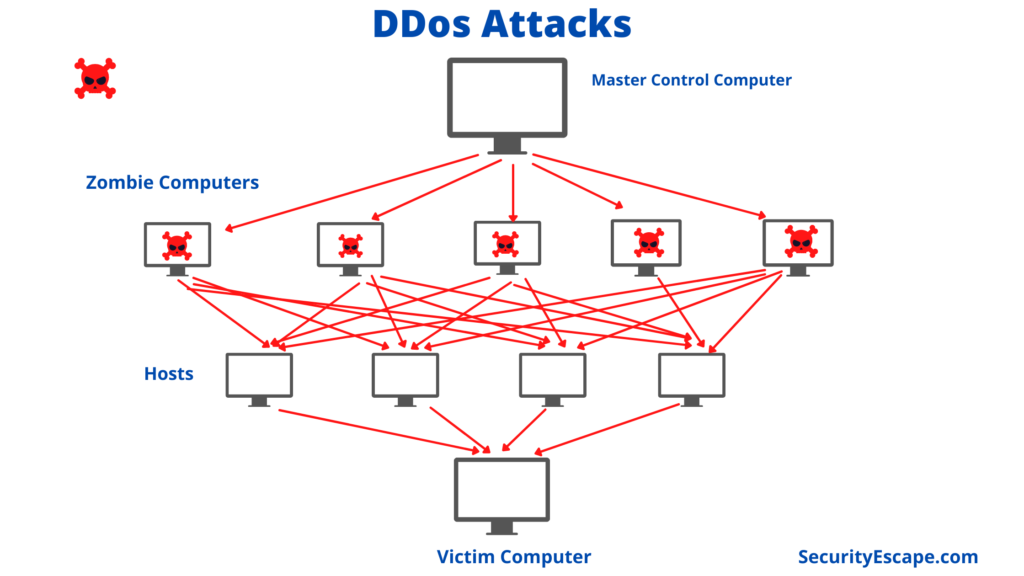
As the picture indicates, there is a “master control computer” that spreads malicious codes to other computers.
After that, the infected computers which are called Zombies, they launch attacks on other computers unknowingly in a distributed and cross-over way.
As a result, the target computer or you can say the victim computer is hit by zombie computers of the botnet.
As a result, the target will become unreachable for some time because receiving thousands of requests from many sources at the same time, it will not be able to process all their requests.
How to Protect Your VPS from Brute Force Attack?
The “Brute Force” attack is another malicious type of attack. This attack can be differentiated on the basis of the final goal which is completely different from the DDoS attack.
The major goal of Brute Force Attack is stealing passwords or data.
The multiple repeated attempts are the working mechanism of this attack that’s why it is called “Brute Force”. The attackers attempt thousands of combinations to identify the password of the victim’s computer.
The aim of brute force attacks is undoubtedly to get control of all your login credentials to your system or server. So that they can steal the data from your computer.
So, what are the main risks involved in this case? Well, The server’s unavailability is one of the main risks in this case. It looks very similar to a DDoS attack, although the purposes are different.
That means many access attempt requests for a prolonged time could cause the final machine to be unable to process all the requests.
Consequently, it may become unavailable or unreachable.
Another major risk is that if the attack gets succeeds, the cyber attacker may get full access to it and use it for different purposes.
Protection Technique
The very effective solution we could find in this case is to use a software application to ban the particular IP addresses of those who try to make a fixed number of authentication attempts after that the attempts fail.
For example, if someone enter a wrong password 5 times to access my VPS, that IP address will be automatically banned, and the system will no longer respond to authentication attempts from that IP.
Then, after a fixed number of days or months, the IP will be unbanned automatically but in this duration, the threat will have been blocked.
How to Protect Your VPS from Generic Setting Problem?
The another type of vulnerability arises due to some “generic” settings that make it easier for cyber attackers to access your server.
Having highly complexed password is definetely a best solution to this problem. It is also a best parctice while setting up the passwords.
The most common passwords used that are absolutely useless against any attack are “1 2 3 4 5 6” or the word “password” itself or “1 2 3 4 5 6 7 8”.
While launching Brute Force attack that hackers try out a list of simplest passwords which are commonly used passwords like above.
If it is one of them, they can easily get access to your system without any effort.
Protection Technique
It is always recommended not to disable the password complexity requirements from the Windows settings because this setting ensures the security of your system, which is very important.
We also suggest changing your password frequently, it will help too because if someone were to steal your password, changing it would make it difficult for them to take control of your system.
Another trick that can be very helpful is to avoid using commonly used names for your computer accounts.
For example, if you are a Windows user, you should avoid using common names such as Administrator or Admin, which is a prebuilt user within Windows and the same applies to your VPS as well.
There are a few services who configure VPS users with names such as Guest User or Root User. These predefined usernames are very dangerous because since they are already available by default in Windows, hackers tend to target Windows prebuilt users guessing that people didn’t change them.
That’s why changing these names makes this type of attack a bit more difficult. The exactly happens with standard access ports.
For Example, Windows Remote Desktop, uses port 3389, and this port is very convenient for hackers because it’s the default port, and many people don’t change it.
It is important to change the port because it can make a huge difference if we talk about the security of your system.
Watch this video to change it quickly.
Final Remarks on How to Protect Your VPS from DDOS Attack
Undoubtedely, implementing these small measures can help a lot.
Also, we have discussed earlier that it’s always recommended to change the password frequently. You can use password complexity checker websites to ensure the proper complexity of your password.
You can create multiple users in your system and can grant it the same privileges as the Administrator user if you want to, but obviously, call it with an unusual name.
At the end of this process, you simply disable the Administrator user you used to log in at the beginning so that it will no longer be possible to use this user with the obvious name.
And also avoid deleting your Administrator Account for future uses.
I gave you an overview of the primary measures you can adopt to protect your cloud server and trading infrastructure.
I hope you may have some understanding about How to Protect Your VPS from DoS, DDoS, and Malware Attack.


