The business concept known as software as a service (SaaS) has been maliciously modified to become Ransomware-as-a-Service (RaaS).
RaaS is a subscription-based business model.
It allows purchasers, known as affiliates, to buy or rent predeveloped tools to carry out ransomware, one of the most common cybersecurity attacks.
Although it operates like SaaS, it is illegal, and both affiliates and RaaS developers operate on black markets.
In this article, we’ll take a look at some of the most significant Ransomware-as-a-Service statistics, including user demographics and attack frequency
Contents
Eye-Opening Ransomware-as-a-Service statistics and facts
- Major players in the RaaS market include Conti, REvil (aka Sodinokibi), DarkSide, Babuk, and Lockbit.
- There were 292 reports of attacks from RaaS affiliates in 2021.
- Phishing emails are the most common delivery method for ransomware-as-a-service.
- 35%+ ransomware groups attacked ICS and OTs.
- In 2021, 60% of ransomware attacks were carried out by RaaS groups.
- Affiliates lunch attacks mostly when organizations are vulnerable (during weekends and holidays).
General Ransomware-as-a-Service Statistics
RaaS is a profitable business model for cybercriminals, with new services popping up regularly.
Its attacks continue to be a significant threat to businesses and individuals worldwide, making it easier for anyone to become a cybercriminal.
Here are Ransomware-as-a-Service stats that will give you a general view of its operation.
1. There was a 36% increase in ransomware attacks in 2022.
(Source: Craft)
In 2021, there were 292 reports of ransomware attacks, with ransom demand increasing to $6.1 million, a 36% increase from the previous year.
Ransomware-as-a-service providers worked together with attackers to largely propagate these attacks and exploit key targets
Attackers and ransomware-as-a-service providers.
2. Attacks during the latter part of 2021 had a pronounced effect on small businesses.
(Source: Coalition)
For small businesses with annual revenues under $25 million, the severity of claims increased 56% overall.
There is a sharp rise in claims frequency, with a 40% increase in ransomware assaults and a 54% increase in money transfer fraud attacks.
3. Ransomware schemes impacted 10 million Android users in 2021
(Source: Zimperium)
Ransomware schemes that targeted Android users impacted 10 million individuals across 70 countries.
Zimperium zLabs reports that at least 200 apps, many of which have managed to get through the security features provided by the Google Play Store, the official repository for Android apps, are malicious.
4. Ransomware-as-a-service offerings can be found on the dark web for as little as $10.
(source: McAfee)
SamSam Group, a cybercriminal group, invested just $10 to get the access link to a major international airport’s security and building automation systems.
However, they charged a $40K ransom for the decryption key.
This Ransomware-as-a-Service stats shows the large ROI received by providers
5. The average downtime for businesses affected by ransomware is 20 days.
(source: Coveware)
In the fourth quarter of 2019, the average downtime increased from 12.1 days to 16.2 days.
However, the time increased to 20 days in the fourth quarter of 2021.
6. In 2020, the FBI reported a 400% increase in reported cyber attacks compared to the previous year.
(Source: Insurance Business)
Ransomware attacks on small to mid-sized businesses have increased by 400% since the outside of the COVID-19 pandemic.
7. In the first quarter of 2022, there was a surge in RaaS groups
(Source: Trend Micro)
Because of the ease of access to cybercrime, there was a significant 63.2% increase in the presence of Ransomware-as-a-Service groups during the first quarter of 2022.
This alarming surge highlights the growing availability of malicious tools and services for criminal activities.
According to the findings of Trend Micro Research, more than 1,200 organizations became victims of targeted attacks in the first half of 2022 alone.
These attacks were orchestrated by over 50 active RaaS and extortion groups, causing widespread damage and financial losses.
Ransomware-as-a-Service Demographics
RaaS has made it easier for criminals to launch ransomware attacks, and the user demographics for these services reflect this.
Some of the most significant statistics for RaaS user demographics include the following:
8. Ransomware-as-a-Service mainly targeted ICS and OT environments in 2022
(Source: Dragos)
RaaS groups targeting Industrial Control Systems (ICS) and Operational Technology (OT) environments rose by 35%, posing a growing threat to critical infrastructure.
Among these attacks, a significant 72% are directed at manufacturing companies, highlighting the heightened risk faced by this sector.
Geographically, 40% of the attacks occurred in the United States, with 32% in Europe and 18% in Asia, demonstrating the global reach of these malicious activities.
9. Singapore had a high rate of attacks from Ransomware-as-a-Service in 2023
(Source: Sophos)
Among those who said attacks hit them, Singapore saw the highest proportion at 84%, followed by South Africa at 78%.
Others are
Spain with 75% attack rate
Switzerland had 75%
US recorded 68%
70% in Australia
73% in India,
58% in Japan
The UK reported the lowest attack rate at 44%.
Note that Singapore and Switzerland had a smaller sample size of 100 each, compared to 500 in the US and 300 each in India and Japan, and 200 in Australia.
10. 71% of Open RaaS attacks occurred against victims with less than 1,000 employees in 2020.
(source: Coveware)
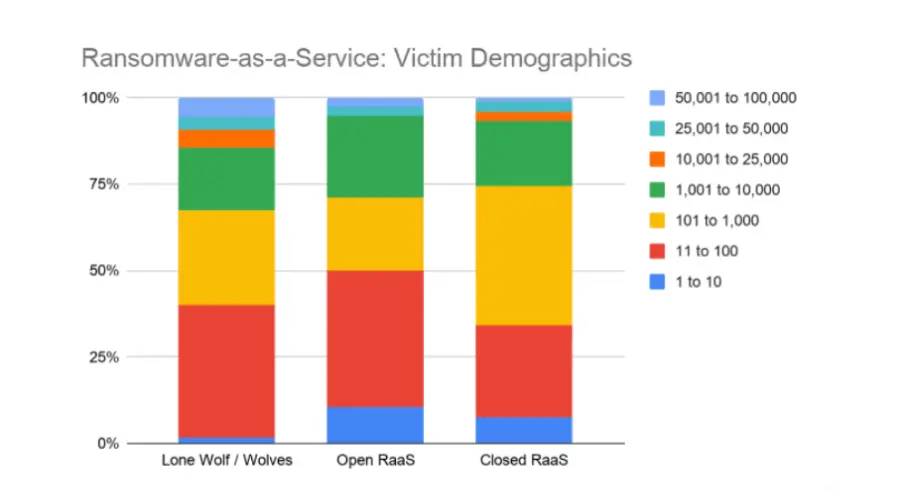
These attackers often resort to cost-effective and simple methods to gain initial access, with nearly 40% of attacks exploiting Remote Desktop Protocol (RDP) intrusion.
This approach allows them to infiltrate networks and establish their foothold.
Closed RaaS has a greater concentration on companies with employee sizes between 101 and 1000.
Their operations utilize larger groups of individuals as affiliates but are highly selective about who they allow distributing the branded ransomware.
11. The US was the most targeted nation by the RaaS groups in Q2 2022.
(Source: Reliaquest)

The United States was the primary target, comprising 38.9% of all victims.
Germany experienced a significant increase of 66.7% since Q1 2022, securing the second spot, closely followed by the United Kingdom with a rise of 16.2%, Italy with an increase of 6.7%, Canada with a surge of 50%, and France with a growth of 26.1%.
These attacks were carried out by Black Basta, Conti, Midware, and a host of others.
12. In Q2 2022, there was a notable increase in attacks across various sectors.
(Source: ReliaQuest)
According to research conducted by ReliaQuest, the industrial goods and services sector experienced 18.4% of all observed attacks.
Following that, the technology sector ranked second with 8.7% of incidents, followed by Construction & Materials with 7.9%, Health Care with 6.4%, and Government with 5.5% sectors.
Notably, the technology sector witnessed a significant increase of 117.9% in targeting, while healthcare organizations saw over twice the number of victims compared to the previous quarter, with a 136.8% increase.
Ransomware-as-a-Service providers statistics
RaaS providers play a significant role in the proliferation of ransomware attacks, offering malicious tools and services to cybercriminals in exchange for a cut of the profits.
Here are some key statistics highlighting the impact and prevalence of Ransomware-as-a-Service providers in the cybersecurity landscape.
13. Cyber pioneered the ransomware-as-a-service model in 2017
(source: ZDNet)
Although Cyber disappeared at the end of 2017, it accounted for 90% of ransomware attacks on Windows.
Cyber is one of the ransomware-as-a-service providers that ever existed.
(Source: Group-IB)
Qilin affiliates use Qilin’s ransomware-as-a-service for illegal activities and can keep 80 percent of the ransom money if it is $3 million or less.
If the ransom amount goes beyond $3 million, the affiliate’s share can increase to 85 percent.
Qilin currently uses a ransomware program developed with the Rust programming language.
Previously, they used a different version based on the Go programming language, allowing them to customize the malware to work on various operating systems like Windows and Linux.
15. BlackCat RaaS affiliates earn more in 2023 than the previous year.
(Source: The Register)
Reportedly, affiliates of the BlackCat ransomware have been earning a higher percentage of the total revenue than that of 2022.
It ranges from 80 to 90 percent, compared to the previous years when affiliates received between 65 to 75 percent of the earnings.
16. Lockbit RaaS group had the most prevalent ransomware attack in 2022.
(Source: Malwarebytes Lab, ThreatSpike)
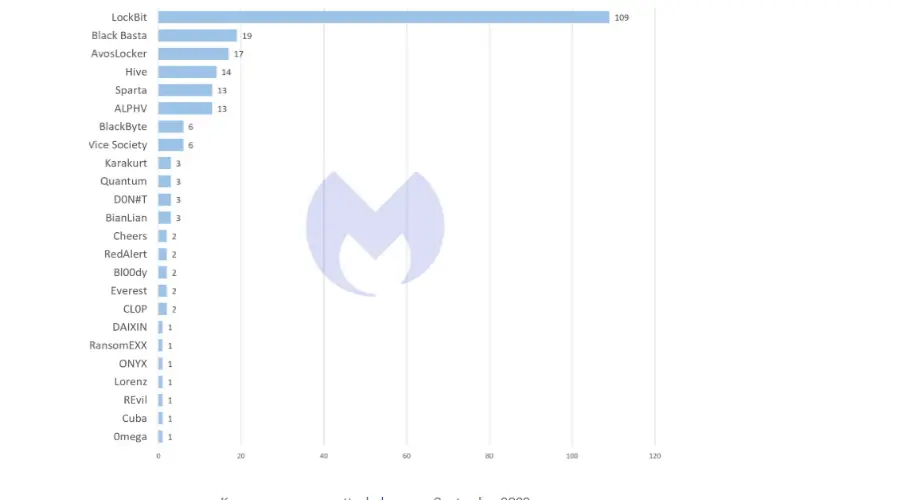
In September, LockBit was responsible for nearly six times the number of attacks compared to the second most widespread ransomware, Black Basta.
In fact, LockBit’s attack volume (109) was nearly equal to the merged attacks of all other ransomware variants, making up approximately 48 percent of the total known attacks.
However, the group released a relentless wave of 51 ransomware attacks, tagged LockBit 3.0, in January 2023 alone, leaving a trail of chaos and despair.
Surpassing all others, they claimed an alarming lead of 28 attacks more than any other ransomware strain, solidifying their position as the reigning threat in the digital underworld.
17. The United States, Italy, and Germany were the most impacted by LockBit in 2020
(Source: Palo Alto Networks)

LockBit 2.0, a malicious cyber threat, has wreaked havoc on companies in different part of the world, with the U.S. having 49.6% of the total impact.
Next on the list was Italy and Germany with 9.6% and 7.9% among its primary targets.
18. In 2020, 45.6% of ransomware attacks by LockBit were on Professional Services
(Source: Palo Alto Networks)
LockBit has zeroed in on industries such as professional services, construction, wholesale and retail, and manufacturing, leaving no sector unharmed.
As the battle for cybersecurity intensifies, the world anxiously awaits whether this sneaky menace will be defeated or if it will plunge us into a new era of digital chaos.
Attack Frequency:
Ransomware attacks are on the rise, and RaaS has made it easier for anyone to launch them.
Some of the most significant ransomware-as-a-service stats regarding attack frequency include the following:
18. Victims are often revisited by their attackers
(Source: OAL)
50% of those who paid attackers to remove ransomware are usually hunted again by Ransomware-as-a-Service affiliates.
However, government authorities, like the FBI, advise victims not to pay ransom to their attackers to reduce the attack cycle.
19. Within 18 months, ransomware-as-a-service hit over half of the organizations in some selected countries in a survey.
(Source: Venture Beat)
A 2021 report by Sophos, a cybersecurity company, shows that ransomware-as-a-service attacks have gained popularity.
The study spans between June 2020 and November 2021.
Venture Beat reported that nearly 60% were carried out by ransomware-as-a-service groups among hundreds of ransomware attacks during that time.
20. Ransomware attacks increased by 150% in 2020, with an attack occurring every 10 seconds.
(Source: Help Net Security)
RaaS attacks accounted for 81% of all ransomware attacks in 2020.
RaaS providers offer services on the dark web, making it difficult for law enforcement to track and shut down these services.
Financial Impact
RaaS has become a lucrative business for cybercriminals, and the revenue generated by these services reflects this.
The average ransom demanded by RaaS operators ranges from a few hundred dollars to hundreds of thousands per attack.
21. The cost of a Ransomware-as-a-Service kit is not foxed
(Source: Crowdstrike)
The price of a RaaS kit ranges from $40 per month to several thousand dollars.
Some well-known examples of RaaS kits include Locky, Goliath, Shark, Stampado, Encryptor, and Jokeroo
22. RaaS operators’ revenue models
(Source: Crowdstrike)
20 – 30% of profits earned in affiliate programs go to the ransomware developer.
However, that isn’t the only source as they get revenues from monthly subscriptions, one-time license fees with no profit sharing, and pure profit sharing models.
23. The LockBit bug bounty program ranges between $1,000 to $1 million.
(Source: Spice Works)
This ransomware-as-a-service statistic highlights the potential profitability for hackers asides from launching attacks.
The reward is given for reporting bugs in LockBit’s website (cross-site scripting or XSS), locker (encryption), and vulnerabilities in Tox Messenger and the Tor Network.
They’re also looking for exceptional ideas to enhance their website and software, welcoming contributions from individuals with innovative suggestions.
24. REvil made one of the largest ransom demands on record
(Source: Crowdstrike, Bleeping Computer)
REvil, alias Sodinokibi, made one of the greatest ransom demands of $10 million in 2020.
As a result, PINCHY SPIDER, a RaaS group that sold the ransomware, earned 40% of the profit made by the affiliate.
Furthermore, the REvil ransomware gang profited over $100 million that year from companies like Travelex, Brown-Forman, Kenneth Cole, etc.
Wrap Up
Ransomware-as-a-Service is a growing industry threatening businesses and individuals worldwide.
As a result of the ease of access to these services, coupled with the potential for significant profits, makes it likely that RaaS will continue to grow in popularity.
Individuals and organizations must protect themselves from ransomware attacks, such as implementing strong cybersecurity measures and regularly backing up data.
Sources:
- Trend Micro
- Insurance Business
- Coveware
- McAfee
- Zimperium
- Coalition
- Craft
- Bleeping Computer
- Crowdstrike
- Sophos
- OAL
- Malwarebytes Lab
- Palo Alto Networks
- ThreatSpike
- The Register
- Group-IB
- ZDNet
- ReliaQuest
- Coveware
- Venture Beat
- Help Net Security
- Sophos
- Dragos
- Spice Works


