Cryptocurrency Scams and Security Tips for Beginners in 2023


In this article, we’re going to be talking about Cryptocurrency scams and Security Tips for Beginners and Existing Users so stay tuned so you can learn about how to keep your crypto safe.
Unfortunately, cyber-crime is all around us scams come in all forms. You could receive an email from somebody claiming that you’ve inherited money from a distant relative or you could receive a text message that looks like it’s from your bank asking to click a link.
Scammers keep getting better at scamming as the world continues to progress into an ever-growing online world. We need to become diligent and know the scams before they reach us so we can easily spot and avoid them.
In this article, we’ll be talking about some of the most popular crypto scams and I’ll be including some tips on how you can stay safe from fake exchanges.
Cryptocurrency Scams and Security Tips
There are many Cryptocurrency scams and Fake Exchanges on the Internet like fake giveaways, fake official Social media accounts on (Facebook, Whatsapp, and Telegram), fake communities and schemes, Crypto-jacking apps and malware but you can ensure your crypto security through proper knowledge and awareness. A few crucial tips are given below that you can follow to maintain secure crypto account.
Fake Exchanges and Apps
Fake exchanges are fraudulent copies of actual exchanges they can look very similar to legitimate exchanges you might think that you downloading the legitimate exchange’s app or clicking on the link that looks like the one that you usually use but you could be mistaken.
These fake exchanges exist for one reason so they can fool you into thinking that you’re using the real deal so that they can steal your money and your personal details.
To keep yourself safe from fake exchanges always bookmark the legitimate exchanges URL and always check the URL before you log In.
For Binance you can use the Binance verify page to check the legitimacy of URLs all Binance groups and social pages can be verified there.
For mobile apps always verify the developer’s details and check comments reviews and the number of downloads. If there are no reviews or comments and the number of downloads is low it’s likely a fake application and this goes for both crypto exchanges and wallets.
Fake Giveaways
If you’ve followed crypto communities online you’ve likely seen fake giveaways typically scammers will ask people to deposit to a crypto address to receive more crypto in return.
There have also been scammers that ask for private keys or other sensitive information. Legitimate crypto giveaways will never ask you to deposit to take part in a giveaway or ask you for private information.
Fake giveaways are usually found on social media platforms scammers comment on posts hoping that somebody will fall for it.
The best way to avoid these scams is to not participate in them, ignore them and move on.
Fake Social Media Accounts
Additionally, people can pose as legitimate companies to create fake social media accounts.
Take a look at the following image can you spot the scam the message from the ad Binance underscore account is a scam.
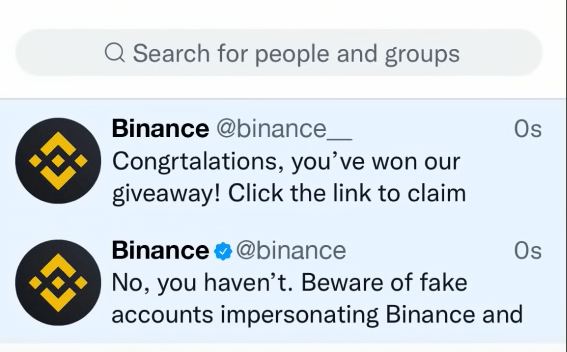
See how easy it is to fake an account and make it look almost identical.
Phishing Attacks
Even if you’re not familiar with online scams, phishing is one that you have undoubtedly heard of. If you haven’t, “Phishing is a type of cyber-attack where scammers pose as a reputable entity or business to deceive people and steal sensitive information.”
Phishing can come in many forms, fake websites, text messages, on social media, and emails. Scammers usually pose as a person or business to try and extract sensitive information from you.
Take a look at this image which one do you think is phishing one of the first places to look when you are not sure about the legitimacy of an email is the email address.
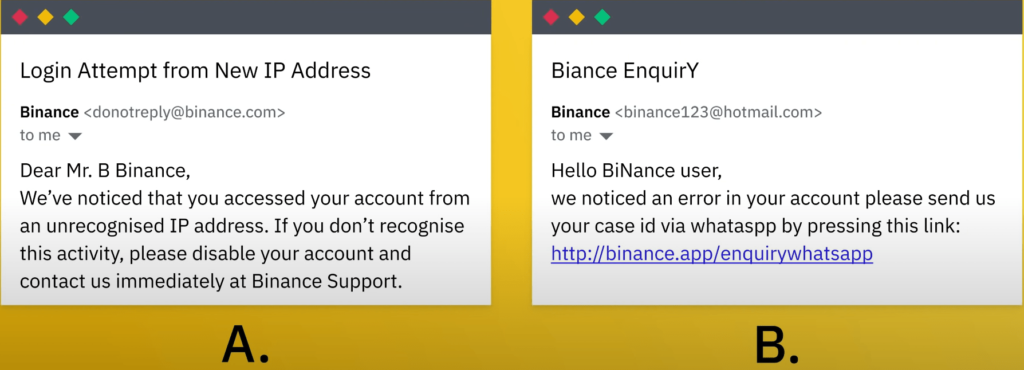
In the image email, a is a binance.com email address and email b is a Hotmail email address this is a clear indication that email b is phishing, additionally, email b requests that details be sent to WhatsApp.
No legitimate business will ask for details to be sent in that way. There is no single playbook that scammers use to get sensitive information.
You could receive a crypto news article that you didn’t subscribe to and then click on the unsubscribe link, just by clicking that link you could be a victim of phishing.
If you suspect an email or message to be a phishing attempt always report it to your email provider and the company that the scammers are impersonating.
Fake Official Telegram and Whatsapp Group
Another common phishing tactic is scammers lurking on official telegram groups for crypto wallets and exchanges.
When people report suspicious activity the scammers will reach out to that person in a personal message posing as a support agent from the group in question encouraging them to share sensitive information like private keys and logging information so they can steal their funds.
You should never share your private keys or your logging information with anyone otherwise they’ll have access to your accounts.
Fake Communities
Whether you enjoy following the crypto community’s influencers or reading crypto news articles and blogs you should never base your trading strategy or your crypto purchases on what someone else says.
You never know what the person or company’s motives are? they could be paid to promote it or they could be investing in it.
It’s good to stay informed but always follow your own advice and never invest more than you can afford to lose.
When looking at a project, questions you should ask are, who is working on that project? does the team have a strong track record? what is the community like and what are they saying about the project?
Once you have a clear view you’ll be better equipped to decide what is best for you.
Copy and paste malware
Another sneaky way for scammers to steal your funds is to copy and paste malware. Malware is malicious software created only to infiltrate your computer or your mobile to cause intentional harm.
Copy and paste malware hijacks your clipboard data a section of RAM where your computer stores copied data. If you are not careful you could send money to an address controlled by scammers.
For example, you want to send bitcoin to a friend your friend copies their address and sends it to you. You copy it and put it in your bitcoin wallet.
If this kind of malware has infected your device the scammer’s address will immediately replace your friend’s address you will then send the scammer’s bitcoin unintentionally.
To avoid this scam consider installing antivirus software, be careful what sites you visit and what you download, and always double-check the address before sending crypto.
Fake Schemes
Two scams as old as money itself are Ponzi schemes and pyramid schemes. A Ponzi scheme is when money is paid from new investors to old investors. When scammers can’t bring new investors the money stops and usually it’s the newer investors that lose the money.
A pyramid scheme is when a person gets paid when onboarding a new member. In most cases, new members have to invest to join the scheme. Once new members can’t be onboarded the money stops and the investments are lost.
The best way to avoid such scams is to do your research on the cryptocurrencies you buy if the currency’s value clearly depending on the number of new joining members you have likely found a Ponzi or pyramid scheme which you should avoid at all costs.
Crypto Jacking apps
Crypto-jacking is when an infected device is being secretly used to mine cryptocurrencies the attacker makes use of the victim’s processing power and bandwidth.
To avoid crypto-jacking only download apps from official app stores monitor your phone for excessive battery draining or overheating. If you notice apps causing this terminate them immediately and always keep your apps updated.
Sim Swapping
Sim swapping is another unsettling way that scammers operate in. The scams mentioned in this article so far you need to take an action for the scam to take effect with sim swapping.
Scammers have been known to use social engineering tactics linked to psychological behavior to trick mobile phone operators into issuing a new sim card to the scammers.
Once they have access to your phone number they can bypass your two-factor authentication and work their way onto your crypto exchange accounts and even crypto wallets sometimes.
The key way to avoid sim swapping is don’t to use text message for two-factor authentication. Use an app like google authenticator instead.
Scammers cannot access apps like these even if they have your phone number. You could also use hardware like a yubi key or a google titan security key for extra protection.
You can also attach a pin or password to your mobile account so that only the person that has that password can make changes to the account.
Additional Security Tips for Cryptocurrency Scams
Here are a few more tips to combat cyber-crime and keep your crypto safe.
- Put a lock on your phone
- Use unique emails for each account
- Make sure that your internet connection is secure
- Install antivirus software
- Only trust secure apps and programs always use two-factor authentication like google authenticator
- Check what devices have been authorized to access your accounts
- Use strong passwords and change them regularly
- Allow crypto withdrawals to only addresses that you trust and check the whitelist regularly
- Use a secure password manager
- Complete KYC on your crypto account
- Consider keeping your funds on a wallet like trust wallet
Final Remarks on Cryptocurrency Scams and Security Tips
We have taken a look at eight different scams and it’s fair to say that the cyber-crime that we are potentially vulnerable to is the stuff of nightmares.
But all is not lost if we remain educated vigilant and do our due diligence, we can avoid scammers taking advantage.
Now you have a few tools in your arsenal to avoid crypto scams. So keep Cryptocurrency Scams and Security Tips into your mind and you are good to go.



User forum
0 messages