Challenges in Cyber Crime Investigation (Detailed Information)


Why cyber-crimes are increasing rapidly? The challenges in the cyber-crime investigation are becoming more complex.
It can be understood by looking at the graph of the number of internet users.
An exponentially increasing number of internet users is the golden opportunity for Hackers, and Spies.
The new and careless internet users are the easiest prey of these malicious entities.
Before discussing the “challenges in the cyber-crime investigation” we should know that “what is a cyber-crime?”
There are many challenges in the cyber-crime investigation because the internet is not bound to a Specific location, state, and country. Cyber-attacks can be launched from any corner of the world to a targeted location. Not every country has strict cybercrime laws. International cyber-crime laws are very weak in case of cyber-attacks launched from a foreign land. The manipulation of cyber data through advanced technologies saves cyber-criminals from punishment. In most critical cyber-crime cases, the victim pulls out his/her hand from the investigation because of fear of privacy exposure.
Quick Summary- Challenges in Cyber-crime Investigation
As the number of internet users increasing, cyber-crime cases also increasing.
Cyber-criminals may target Industries, Businesses, government Organizations, Healthcare data, and common people.
Cybercrimes are conducted through Phishing Pages, Spam links, OTP Exposure, Wi-Fi hacking, unsecured web pages, Virus injection, and unsecured software installation.
It is extremely challenging to identify, investigate and punish cyber-criminal as they are not bound to Geographical limits.
They manipulate cyber data using advanced technologies that make their tracking difficult.
The national and international laws are either weak or Poorly implemented which makes the investigation more difficult.
Cyber-criminals have an edge over victims as they may have victim’s private/ useful data. This factor also affects the investigation.
Bad Intergovernmental understanding between two countries plays a pivotal role in the investigation.
It is most challenging to Investigate and punish cyber-criminal who are backed by the country’s government.
Cyber-criminals demand payments in cryptocurrencies that are untraceable.
In most Cyber-crime cases the victim pulls out from investigation from the fear of Privacy exposure or useful data destruction.
What is Cyber-crime?
Spreading or injecting any malicious codes like software, malware, images, links, and illegal information to computers, networks, or networked devices is called Cyber-crime.
Cyber-criminals target devices to steal information, damage/ disable the device for profit generation.
The reasons behind the increase in the pace and volume of cyber-crime are the speed of the internet, anonymity, and convenience.
Now it is much easier to commit cyber-crimes like Money-laundering, harassment, ransomware, and fraud.
Cyber-crime Statistics
Let’s see what Cyber-crime statics say
America’s biggest oil Pipeline “Colonial Pipeline” faced a huge cyber-attack recently and lost $4.4M.
In another case, America’s Federal Reserve Bank faced a giant cyber-attack and lost $80.1M.
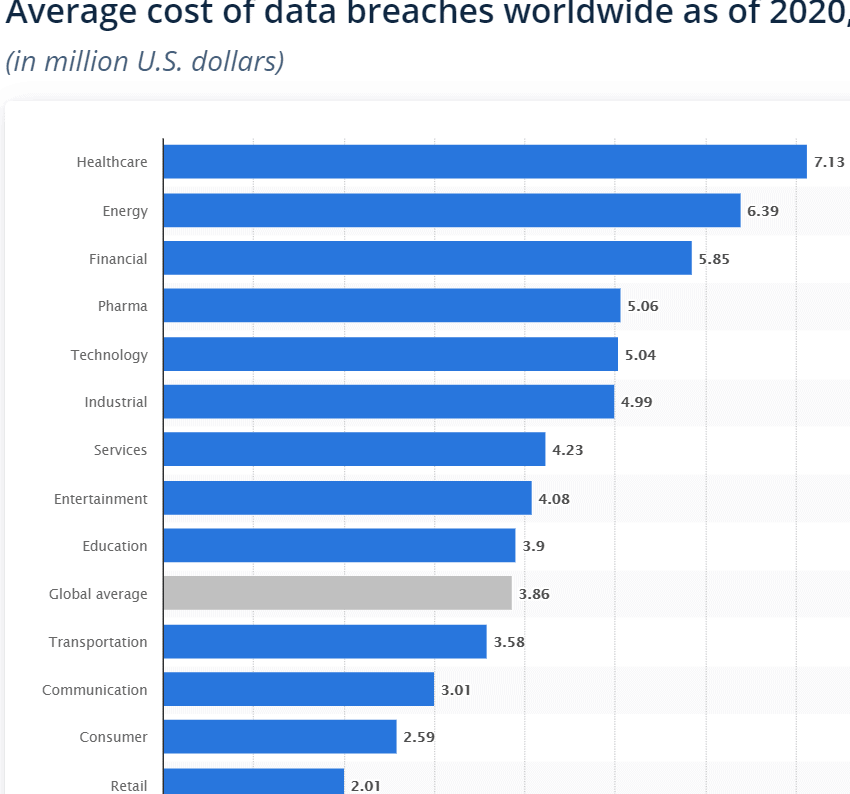
According to Statista “Average cost of Data Breach Worldwide (2020) by industry”
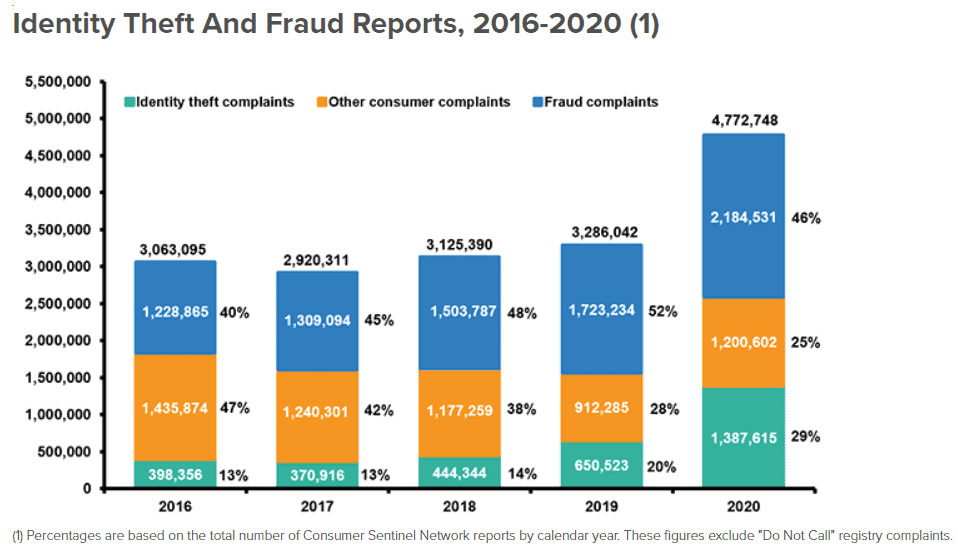
According to iii.org “Statistics of identity theft and Cyber-crime in the USA”
For Detailed Statistics Refer to varonis.com “Detailed Statics” and Cloudwards.net “Cybersecurity Statics“
Businesses, Government organizations, and common citizens face Billions of dollars’ loss just because of cyber-crimes.
Challenges in Cyber-crime Investigation
Being a cyber-crime victim is always like a nightmare, sometimes it takes a decade to recover from Identity theft.
But the cyber-crime investigation is even more challenging than facing Identity theft.
Cybercrime is a global threat because cyber-attacks can be launched from any corner of the world to any specific targeted location.
The most challenging task is to investigate cyber-crime because the factors mentioned below are involved.
A) Weak International Cyber-crime Laws
International cyber-crime laws are too weak to punish a cyber-criminal.
Even an investigation can’t be initiated on the basis of international cyber-crime laws.
If a cyber-criminal belongs to a foreign land, It is almost impossible to punish him.
Sometimes a cyber-criminal is known to security agencies but the Government of the specific country doesn’t allow the prosecution.
B) Boundless Internet
Internet is not bound to the Geographical limits of a specific country or state.
A cyber-crime can be commissioned from a corner of the world to another corner.
And searching for a criminal in this scenario is like “Shooting the birds in the dark”.
C) Challenges of Data Loss in Cyber Crime Investigation
Many European countries follow strict Data Privacy laws and these laws block the Investigation process.
Network operators don’t breach their user’s data that leads to a severe impact on the cyber-crime investigation.
Sometimes lack of data causes delay or discontinuity in the investigation process.
D) Anonymity Challenges in Cyber crime Investigation
The development in technology is useful for both victims and criminals.
Cybercriminals use some tools to hide the physical location that makes them anonymous.
These tools are also responsible for making investigation even more challenging.
E) Advanced Technology Challenge in Cyber Crime Investigation
Cybercriminals are committing crimes even more frequently and precisely by the use of the latest advanced technologies.
These technologies not only help criminals to commit crimes but hide their identity also.
These technologies are
- High Speed Internet
- Data Encryption software
- Artificial Intelligence
- Use of VPN
F) National Criminal Laws
A country’s internal cyber-crime laws also play a pivotal role in the investigation.
Cyber-crime investigation becomes more challenging if a country has weak cyber-crime laws.
Like in European countries follow GDPR law (Strong Data Privacy law) that hinders the cyber-crime investigation.
G) Public-Private Partnership- Challenges in cyber-crime investigation
One of the major challenges in the cyber-crime investigation is the lack of proper cooperation between public and private organizations.
Lack of cooperation between Public-Private Partnership arises due to poorly implemented legal framework.
This issue may cause delays in cyber-crime investigations.
How cyber-crime works?
Cyber-criminals target rich-companies and common people and install specific ransomware (Called “Stop”) to their network or device.
There are a few more ransomware like Screen lockers and Encryption ransomware.
The Stop ransomware stops all the activity on a network or device.
The Screen lockers lock the device screen until the payment is made.
And encryption ransomware encrypts all the data in the device.
In all cases payment is requested through virtual currency to Recover Encrypted files from Ransomware.
Other cyber-crime activities are committed through the methods mentioned below
A) Accessing Unsecured Websites
The websites having no HTTPS are considered unsecured websites.
And providing your sensitive data (Like Payment details) on these websites may cause data theft and cyber-attacks.
B) Clicking suspicious links
Messages, emails, webpages, images, and videos containing suspicious links are extremely dangerous.
Clicking these links may cause losing control, and hacking of devices or networks.
Sometimes these links lead to phishing pages that may cause Privacy exposure or sensitive data theft.
C) Using Public Wi-Fi
Public Wi-Fis are considered as one of the most favorite places for hackers and cyber-criminals.
Using public Wi-Fi without additional security measures like VPNs is full of risks.
Cyber-criminals keep close eyes on such places, as these Wi-Fi connections are easy to hack.
And sharing sensitive data over public Wi-Fi may cause critical security risks.
D) OTP Exposure
Transaction through One Time password (OTP) is very popular and extensively used throughout the world.
But exposing your Time password may cause serious cybersecurity risks.
OTP exposure to an unknown may critically affect your financial state.
E) Downloading and Installing Suspicious software
Downloading and installing software from unverified sources may cause the spread of spyware, malware, and virus into your device.
This unwanted software may slow down your device, and spying your sensitive information.
And in some critical cases, it may breach your sensitive data or take complete control of your device.
How to Report/ Complaint Cyber-crime?
There are many web portals run by the government where you can file complaints against cyber-crime.
The cyber-cell will contact you and will ask about the incident.
If cyber-crime is related to your bank account, it is recommended to contact your bank first and ask them to block Debit or Credit cards.
You can also file a complaint at the nearest police station.
How cyber-crime can be prevented?
There are a few recommendations that every internet user should follow to avoid becoming a cyber-crime victim.
- Avoid sharing sensitive data over Public Wi-Fi
- Never click unknown or spam links
- Avoid sharing sensitive data on unsecured websites (Without HTTPS)
- Never share your OTP to an unknown.
- Clear your browsing history on regular basis
- Use VPN
How cyber-crime becomes a national concern?
Cyber-criminal not only target common citizens, But they target Government Organizations and Business Institutions also.
Cyber-criminals may steal confidential information from government organizations and it may become a threat to national security.
In recent days the cyber-attacks on government organizations have increased dramatically and this is a matter of concern for a country.
The Final Words on Challenges in Cyber-crime Investigation
Cyber-crimes are increasing dramatically and the need of the hour is to ensure data security and privacy. As we discussed earlier “the challenges in the cyber-crime investigation”,
The only way to avoid the nightmare of becoming a cybercrime victim is to follow the security recommendations.
Cybercrimes can’t be controlled completely it can only be prevented by applying recommended security measures.
Informing the cyber-cell immediately about a cyber-crime may save you from criticality.
Always use Original and updated versions of the operating system and software from authorized websites only.
What do you think about this issue and the article? Please share your opinion in the comment section.



User forum
0 messages